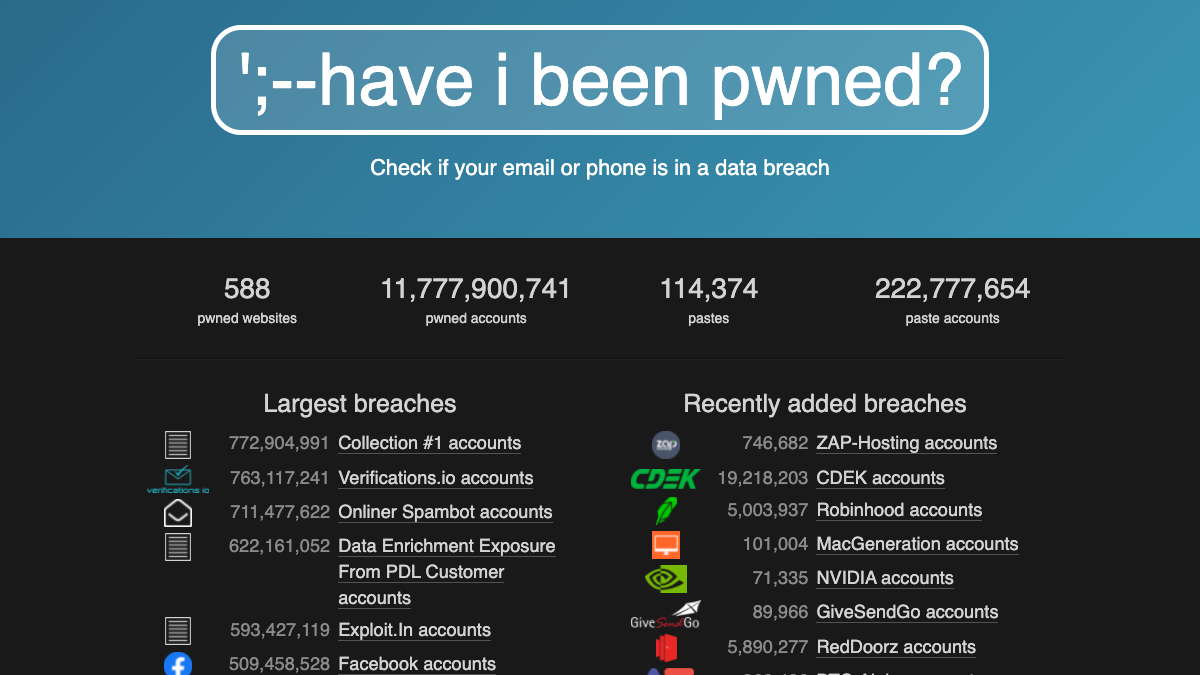
While FastBound has never had a security breach, you have undoubtedly heard of sites that have. As of July 2018, Troy Hunt’s Have I Been Pwned (HIBP) site has collected more than 11.7 billion compromised (aka pwned) accounts compiled from 588 website breaches and more than 114 thousand pastes of more than 222 million accounts alone. Data breaches have taught us 1) that most people don’t use a password manager and 2) humans love to reuse their passwords. Reusing passwords is extremely risky. It’s so prevalent because it’s really easy to do, and people aren’t aware of the potential impact.
Credential Stuffing Attacks
Attacks such as credential stuffing take advantage of reused credentials by automating login attempts against systems using known emails and password combinations.
Consumers have no control or insight into how companies store their passwords. When they have a data breach, the email addresses and passwords are then made available for attackers to try at other sites and apps.
Password Manager
Using a password manager like 1Password or BitWarden to Generate long, strong, and unique passwords for each site you have a login for will significantly reduce your risk of falling victim to a credential stuffing attack.
Complexity adds unnecessary complexity
Current NIST password guidelines suggest that you focus primarily on password length instead of the complexity when creating passwords. Ironically, using complex passwords (adding special characters, capitalization, and numbers) makes it easier to guess your password. Complex passwords are harder to remember, which means users may need to update their passwords more often, making minor changes, making them easier prey for cyber attacks. NIST requires an 8-character minimum for passwords.
Don’t allow previously breached passwords
In August 2017, The National Institute of Standards and Technology (NIST) released guidance recommending that user-provided passwords be checked against existing data breaches. The rationale for this advice and suggestions for how applications may leverage this data are detailed in Troy Hunt’s Introducing 306 Million Freely Downloadable Pwned Passwords blog post.
Accordingly, when you set a password for the first time, change your password, or reset your password, we check to ensure that your password is not among the 11.7+ billion Pwned Passwords. If your password has been seen in a data breach, FastBound asks you to pick another one. FastBound also checks if your password has been breached when you log in to FastBound. If you log in with a breached password, we’ll let you know and guide you through changing it. If you use that same password on other websites, you should be changing it there, too. It would be best to use a random password generated by your password manager.
If you are curious about how we check your password against billions of breached passwords without breaching your password, protecting the privacy of searched passwords, check out Troy’s blog post about Cloudflare, Privacy, and k-Anonymity. It gets a little technical, but it’s worth the read.